
Andres Knobel ■ The role of banks and digitalised beneficial ownership registries: way more than just reporting discrepancies

On 14 July the Tax Justice Network co-hosted the fourth call of the multi-stakeholder group to promote beneficial ownership verification. We took the opportunity to present updates on progress of the pilot in one African country and to hear more presentations on how to verify information (our last call included 15 brilliant presentations on strategies used by authorities, banks and researchers.)
This time, the call’s presentations covered two main topics: how to share confidential information and how to apply advanced analytics to already collected data to detect red flags.
As we described in our paper on beneficial ownership verification, one of the steps to confirm the accuracy of the data involves cross-checking information against other databases. “Is John really called John and does he actually live on that street?” Countries are already required to ensure national authorities cooperate and share information with each other (eg the tax authorities and the financial intelligence unit which deals with money laundering). Achieving this at the national level is already challenging due to the lack of standardised data or interconnection of local databases, along with the refusal of local authorities to cooperate with each other by invoking fiscal confidentiality or other secrecy laws (they tend to forget that they all play for the same team, and that many of these financial crimes are related to each other, eg tax evasion may be a predicate offense for money laundering).
Sharing confidential information with other parties
Given the current freedom of establishment where anyone may have interests in a legal vehicle from any country, domestic cooperation is not enough. Countries need to verify information on any non-resident beneficial owner: “Hi Germany, is Friedrich really called that, and does he actually live in Berlin?” Cooperation at the international level may be even more difficult because countries would likely be unable and unwilling to share personal data of their citizens/residents with any foreign country. To address this, our paper had proposed zero-knowledge proof queries, where the beneficial ownership register of say, the UK, would automatically query Germany’s databases on the details declared by Friedrich to the UK register. German databases would only answer whether there was a perfect match (confirming that Friedrich didn’t lie to the UK). In case of a mismatch, Germany wouldn’t reveal the true answer. The UK would simply reject Friedrich’s registration until he declares information that results in a perfect match with Germany’s records.
An alternative to our proposed zero-knowledge proof queries was presented on the call by Jules Anthonia from FCInet. It suggested enabling cross-border checks without the need for foreign databases to be integrated. “FCInet is a non-commercial (government developed) decentralised computer system that enables FCISs (Financial Criminal Investigation Services) from different jurisdictions to work together, while respecting each other’s local autonomy. With FCInet, FCISs can jointly connect information, without the need to surrender data or control to a central database or authority, and without unlawful intrusion on privacy. A core functionality of FCInet that allows FCISs to jointly analyse information and to identify relevant information in real time, is ma3tch. Ma3tch enables distributed analysis without the need to bring data together in one central place.”
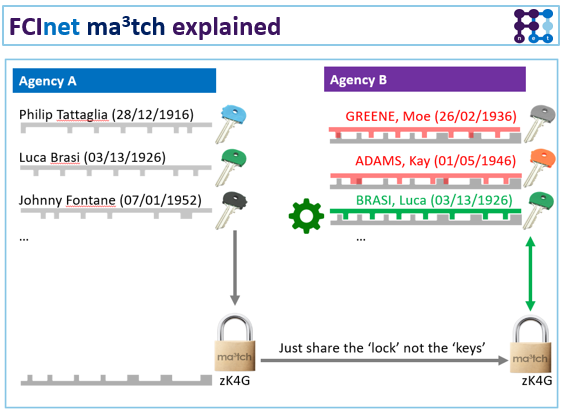
While this technology is meant for financial intelligence units and tax authorities, it could also be used by beneficial ownership registries, as the figure shows. Ma3tch agents (Agency A) would pseudonymise local data (Philip Tattaglia, Luca Brasi and Johnny Fontane) into match filters (zK4G). The receiving register (Agency B) matches its local data (Greene Moe, Adams Kay, Brasi Luca) against the received filter in FCInet. Only hits on information that both the sending FCIS and the receiving FCIS have in common are revealed (eg Luca Brasi). Subsequently, identified hits can be validated and followed up, so that Agency B only shares information about Luca Brasi.
Similar technologies could be used to share information among private actors. Under the 5th EU Anti-Money Laundering Directive (AMLD 5), banks are required to report discrepancies to the public beneficial ownership registers. If company A registered John as its beneficial owner in the beneficial ownership register but then, when opening a bank account, company A tells the bank that Mary is its beneficial owner, the bank should report this discrepancy.
However, banks could report discrepancies not only with the beneficial ownership register, but among themselves, for example if company A told bank 1 that John is the beneficial owner, but when declaring to bank 2, it said that Paul is the beneficial owner. The UK Financial Conduct Authority (FCA) organised a TechSprint where different banks, compliance and data companies proposed frameworks on how banks could share customer information with each other in an encrypted way so as to detect discrepancies without disclosing their customers’ personal data.
Detecting red-flags using banking information
While reporting discrepancies in beneficial ownership between different data sets is useful, it’s not enough. After all, a company could have declared John as the beneficial owner to the beneficial ownership register and to all banks, when actually John is a de facto nominee and the real beneficial owner is Mary. There would be no discrepancies, but the data would still be wrong. More sophisticated checks are also necessary, especially in looking for patterns and red flags, as described in our paper on beneficial ownership verification.
On the one hand, outliers would be revealed if countries knew what their typical corporate ownership structure looks like. As example on how to do this, we undertook research using Orbis data to explore the legal ownership chains of UK companies.
There is significant scope, however, to look to internal information to verify accuracy of external information provided. Banks have key financial information that if examined in the right way could also detect money laundering schemes and enable real beneficial owners to be identified. Based on their experience analysing the Moldova Laundromat and other major money laundering schemes, Howard Cooper, Chris Ives and Matt Weitz from Kroll described how banks could enhance their analysis to detect sophisticated financial crimes.
Rather than analysing customers and their transactions in isolation – eg “has company X done too many transactions above $10,000?” – banks should look at the full customer profile across their full customer base to identify patterns and hidden relationships. This way it will be possible to determine whether apparently unrelated bank customers are linked to one another. These checks could include analysis to detect overlap in common customer information such as addresses, telephone numbers or IP addresses (from where remote bank transactions are carried out) as well as shared people – directors, shareholders, signatories, beneficial owners, people with power of attorney or professional service providers who opened the account on behalf of the company. Even more sophisticated analysis would involve analysing fund flows to detect undeclared links between customers and the ultimate beneficiary of transactions.
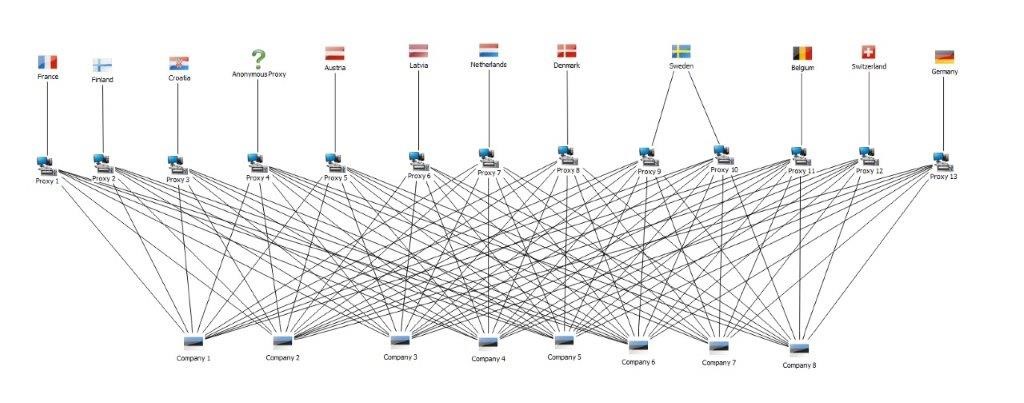
For example, in one Kroll investigation into a complex fraud and money laundering network, the analysis of internet banking IP addresses (in the middle of the picture below) revealed connections across a large number of purportedly unrelated customers (at the bottom):
Another example involved looking at apparently unrelated customers (in green, blue and pink) that shared the same corporate nominee directors and shareholders, which were owned and controlled by the same trust and company service provider:
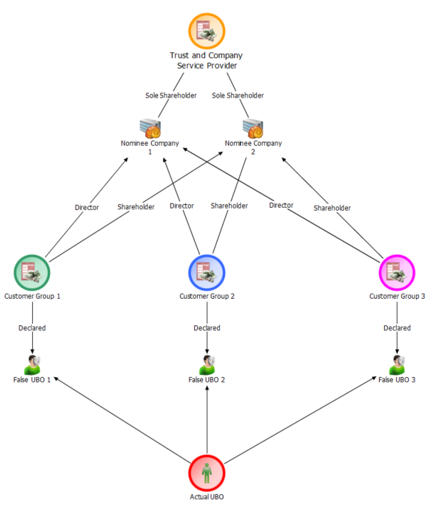
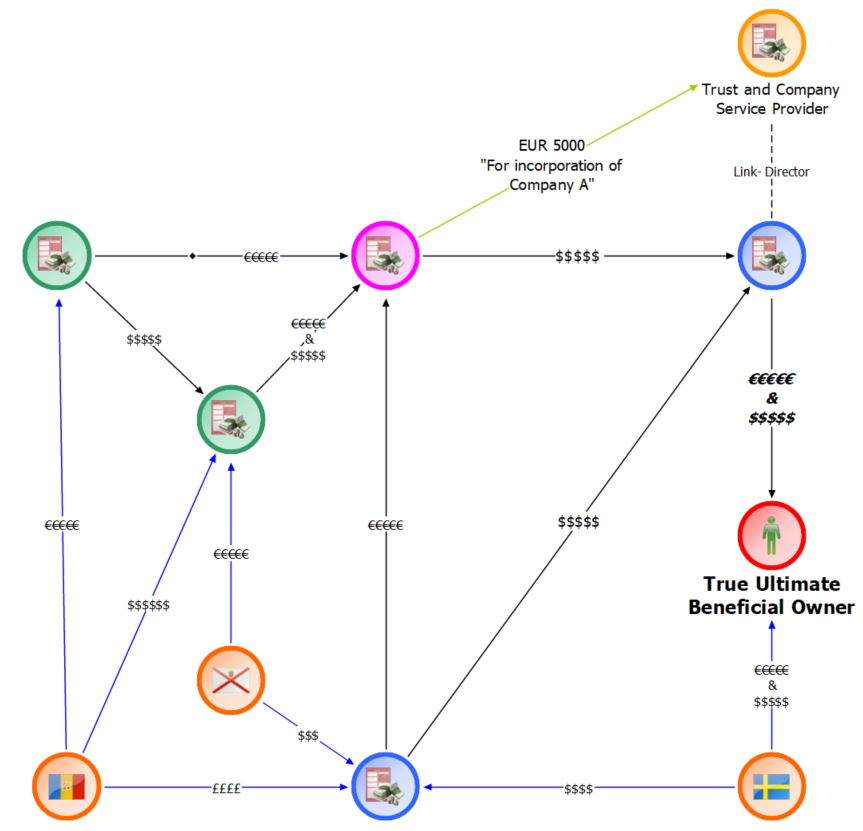
On the surface, and in know-your-customer (KYC) files and the relevant corporate registry documents, all three of the customers had different beneficial owners. However, by analysing the transactions of the customers together rather than separately, it was quickly revealed that:
- The three customers received funds from common external accounts and the onward movement of funds followed the same pattern, exposing an undeclared relationship between them.
- One customer (in purple) transferred funds to the Trust and Company Service Provider for the incorporation of another apparently unrelated customer (in blue), indicating the know-your-customer (KYC) information may not have been accurate.
- The end result of all the transactions was the transfer of funds to the account of an individual (in red) – indicating that this individual was the true ultimate beneficial owner of the companies and that the transfers were contrived for their benefit.
Looking at each transaction in isolation would not reveal any issues, it was only by examining the network of transactions did the discrepancies between the know-your-customer (KYC) data and the actual beneficiary of transactions become apparent.
Other red-flags that digitalisation makes possible to detect
By digitalising administrative procedures, countries may not only prevent corruption, because there is no paper file to be lost or changed, but they may also look for patterns and outliers to detect red flags.
Maria Jose Martelo and Eduardo Martelli, formerly at Argentina’s Federal Ministry of Modernisation explained how the digitalisation of administrative procedures in Argentina enabled two basic red-flags to be detected: one based on time and the other based on the responsible public officer.
Regarding time checks, two indicators can be constructed. The first one looks at compliance with “First in, first out” (FIFO). In principle, unless a procedure is categorised as urgent, chronological order should be respected. If John started the application to set up a company on 1 April, and Paul started another on 10 April, there should be no reason why Paul’s company should be ready first, assuming John’s application had no flaws. If this happens, it may be an indication that Paul bribed someone to get his company ready first, or that John was blackmailed by the public officer to pay a bribe, and upon his refusal, his application was put on hold (or “in a drawer” as the Argentine expression goes).
Similarly, by looking at specific procedures throughout the year, it is possible to determine the average time it takes to complete one. Applications (to set up a company, get a construction permit, etc) that are too brief compared to the average time may be an indication of corruption (eg bribe or conflict of interest). On the other hand, an application that is taking too long may be an indication of blackmail or the application being slowed down to encourage the applicant to bribe the public officer.
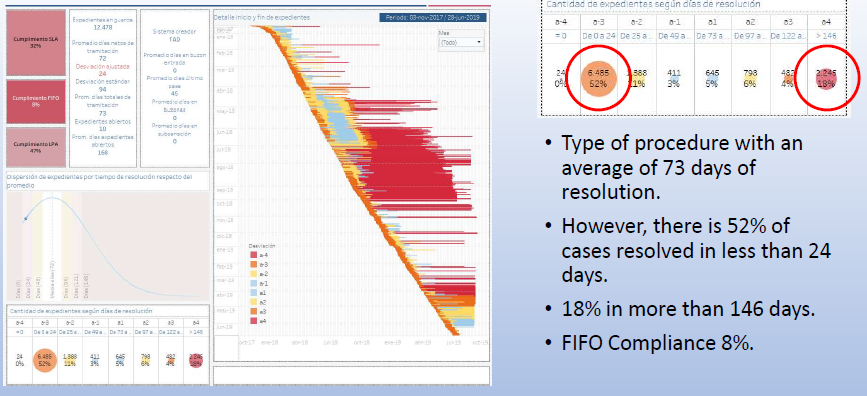
These time checks may be combined with an association check, to determine whether the same corporate user (or service provider) always gets the same public officer to process their application. This would be especially suspicious if that public officer also takes a record (short) time in approving the applications.
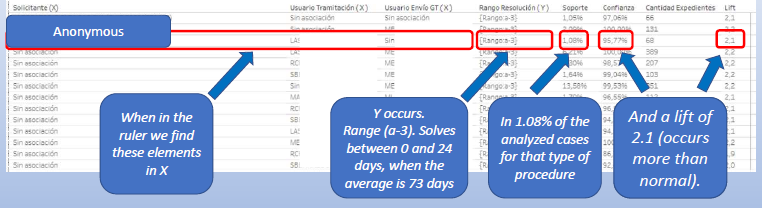
While none of these rules would confirm a case of corruption (after all, a fast public officer may simply be more efficient than the rest, or may be specialised to deal with specific types of industries or cases), at the very least such red flags should prompt an investigation to discount any collusion or corruption.
Importantly, these digitalised checks only work if absolutely all procedures are done digitally. By allowing any exception to the rule, a window for corruption is opened. Unfortunately, Argentina invoked problems with the IT platform at the beginning of the Covid-19 pandemic (after the platform exposed a scandal of overpriced contracts) to allow paper-based procedures to take place again.
Conclusion
Countries and policymakers should consider the following proposals:
- Digitalised procedures and data (eg digitalised beneficial ownership registers) allow the cross-checking of information and the detection of red flags (eg based on time analysis and association rules).
- By combining digitalised data and encryption, it is possible to share confidential information and detect discrepancies without disclosing all the personal details of shareholders, beneficial owners or relevant users. This would enable cross-checks among countries and among private holders of information.
- Banks have a trove of data that should become part of systematic anti-money laundering checks so that they report not only basic discrepancies, but also other undetected cases of wrongful beneficial ownership information. These checks could include analysis to detect overlap in common customer information such as addresses, telephone numbers or IP addresses (from where remote bank transactions are carried out) as well as shared people – directors, shareholders, signatories, beneficial owners, people with power of attorney or professional service providers who opened the account on behalf of the company. Even more sophisticated analysis would involve analysing fund flows to detect undeclared links between customers and the ultimate beneficiary of transactions. While this analysis would be done at each bank, these checks should also be done at the global level, as we proposed in our recommendations for SWIFT to include beneficial ownership information in the messaging system and to run similar advanced analytics.
Related articles

The elephant in the room of business & human rights
The elephant in the room of business & human rights
UN submission: Tax justice and the financing of children’s right to education
14 July 2025

How the UN Model Tax Treaty shapes the UN Tax Convention behind the scenes
The 2025 update of the UN Model Tax Convention
9 July 2025
One-page policy briefs: ABC policy reforms and human rights in the UN tax convention

Bad Medicine: A Clear Prescription = tax transparency
Tax justice pays dividends – fair corporate taxation grows jobs, shrinks inequality

Reclaiming tax sovereignty to transform global climate finance
Reclaiming tax sovereignty to transform global climate finance
16 June 2025

